Passwordless Authentication
Gain access without entering a password or answering security questions
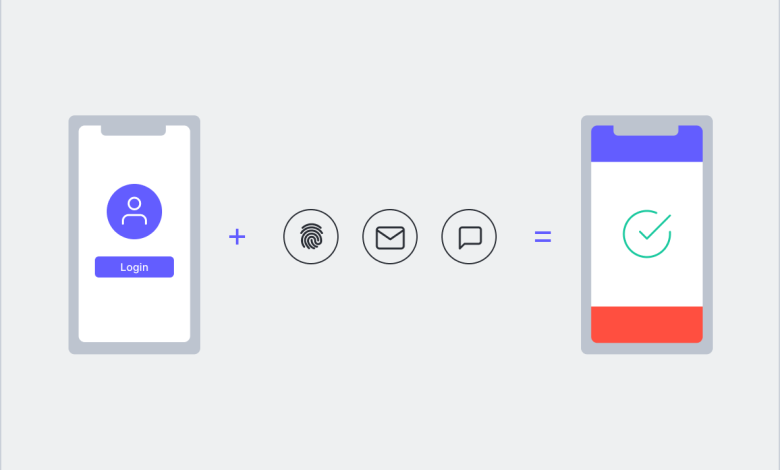
What is Passwordless Authentication?
Passwordless Authentication is an authentication method that allows a user to gain access to an application or IT system without entering a password or answering security questions. Instead, the user provides some other form of evidence such as a fingerprint, proximity badge, or hardware token code. Passwordless Authentication is often used in conjunction with Multi-Factor Authentication (MFA) and Single Sign-On solutions to improve the user experience, strengthen security, and reduce IT operations expense and complexity.
The Problem with Passwords
Today’s digital workers rely on a wide variety of applications to perform their jobs. Users are forced to memorize and track a dizzying array of frequently changing passwords. Overwhelmed by password sprawl, many users take risky shortcuts like using the same password for all applications, using weak passwords, repeating passwords, or posting passwords on sticky notes. Bad actors can take advantage of lax password management practices to mount cyberattacks and steal confidential data. In fact, compromised account credentials are a leading cause of data breaches.
Simple authentication methods that require only username and password combinations are inherently vulnerable. Attackers can guess or steal credentials and gain access to sensitive information and IT systems using a variety of techniques, including:
- Brute force methods – using programs to generate random username/password combinations or exploit common weak passwords like 123456
- Credential stuffing – using stolen or leaked credentials from one account to gain access to other accounts (people often use the same username/password combination for many accounts)
- Phishing – using bogus emails or text messages to trick a victim into replying with their credentials
- Keylogging – installing malware on a computer to capture username/password keystrokes
- Man-in-the-middle attacks – intercepting communications streams (over public WiFi, for example) and replaying credentials
Passwordless Authentication Reduces Risk and Improves User Satisfaction
Passwordless Authentication strengthens security by eliminating risky password management practices and reducing attack vectors. It also improves user experiences by eliminating password and secrets fatigue. With Passwordless Authentication, there are no passwords to memorize or security question answers to remember. Users can conveniently and securely access applications and services using other authentication methods such as:
- Proximity badges, physical tokens, or USB devices (FIDO2-compliant keys)
- Software tokens or certificates
- Fingerprint, voice or facial recognition, or retina scanning
- A mobile phone application
Passwordless Authentication is typically deployed in conjunction with Single Sign-On, so an employee can use the same proximity badge, security token, or mobile app to access all their enterprise applications and services. Passwordless Authentication is also often used as part of a Multi-Factor Authentication solution, where users are forced to provide multiple forms of evidence to gain access to enterprise applications and systems. For example, to access a mobile phone app, a remote user might be required to tap a fingerprint sensor and enter a one-time, short-lived SMS code sent to their phone.
The latest MFA solutions support adaptive authentication methods, using contextual information (location, time-of-day, IP address, device type, etc.) and business rules to determine which authentication factors to apply to a particular user in a specific situation. Adaptive MFA balances convenience with security. For example, an employee accessing an enterprise application from a trusted home computer might be required to provide only one form of authentication. But to access the application from a foreign country over an untrusted WiFi connection, the user might also have to enter an SMS code.
Passwordless Authentication Benefits
Passwordless Authentication provides a variety of functional and business benefits. It helps organizations:
- Improve user experiences – by eliminating password and secrets fatigue, and providing unified access to all applications and services.
- Strengthen security – by eliminating risky password management techniques and reducing credential theft and impersonation
- Simplify IT operations – by eliminating the n.eed to issue, secure, rotate, reset, and manage passwords.
What is OwnID?
Rooly Eliezerov is a serial entrepreneur in the digital identity space, currently the Co-founder of OwnID, the passwordless identity platform. Prior to OwnID, Rooly co-founded Gigya, which was acquired by SAP. Gigya leads the Customer Identity and Access Management (CIAM) market, managing over a billion digital identities for the largest organizations in the world. The book ‘The Digital Identity Crisis’ by Rooly Eliezerov was published by Wiley and Sons in March 2018.
In this superb interview, co-founder of OwnID, Rooly Eliezerov, provides a behind-the-scenes look at his new, innovative startup’s smartphone-based, biometric passwordless authentication technology. OwnID aims to transform how people log into their accounts, and to drive advances in the digital identity ownership arena.
Decentralized solutions like OwnID pave the way towards a self-sovereign identity and hyper-personalized user experiences. Discover how the identity management landscape is evolving, and see what the future might hold.
Tell us about the OwnID story
Dor and I, the founders of OwnID, are part of the founding team of Gigya, the Customer Identity and Access Management (CIAM) platform that was acquired by SAP in 2017 for $350 million. After the acquisition we felt that identity management is an unfinished business and that there needs to be a more transformational approach to identity. We joined forces with some other bright minds from Gigya and raised our seed round with the main Gigya investor Mayfield. So, the band is back together for Act 2.
Why biometrics as opposed to another sign-in methodology?
Our concept is that ‘the phone is the key’. In the same way my phone can unlock my car and house door, it can unlock anything else digital. Fortunately, phones are locked with a secure biometric mechanism, and therefore what we have here is frictionless Two Factor Authentication (something you have + something you are). We believe it’s much better than old school auth mechanisms like magic links, SMS code and definitely a password. Better means: easier to use and more secure.
Tell us about the technology behind the product?
We are utilizing WebAuthn and FIDO2. Therefore, our product is completely web based. It enables websites accessing the lock mechanism of the user’s phone (both iPhone and Android). But our product goes beyond the core technology. It addresses many use cases (e.g. phone temporarily not available, phone is lost, phone doesn’t support biometrics, user already has an account with a password etc.)
How do organizations add passwordless to their customer identity processes?
A big advantage of OwnID is the ease of implementation. OwnID is an add-on to a given site’s existing system. Sites that wish to add OwnID’s passwordless can keep their existing registration and login forms, and just add the OwnID button side by side with their password field, which enables the users to authenticate using their phone’s biometrics. If user is browsing their desktop or any other device, when clicking this button, a QR code will be presented, the user will scan it with their phone which will prompt their phone’s FaceID/fingerprint, and the desktop will be logged in.
What impact is the OwnID technology having?
Many more users register and login when they can do it with their phone biometrics. It’s just easier. See how it’s done on Nestle and Delonghi. These two of OwnID’s largest clients report an increase in both registrations and logins to their sites and are constantly deploying OwnID to additional properties around the globe.
What key principles do you think about in protecting your users’ data?
Our key principle is: don’t keep data in a single place, but rather, distribute it. Therefore, we don’t store any user data in our database. We don’t even have a user data base. Our technology keeps the user auth keys on the user’s phone. We place a public key for each user in the database of the website we are serving, and we match a signature that is generated by the user’s phone to the public key. For each website the user has different keys.
What business insights would you like to share with other business leaders?
Our business approach is adoption driven. We believe that elegant solutions are not enough. As a matter of fact, our product strategy is strongly influenced by the go-to-market strategy. This is why we chose to offer our solution as an add-on and not a reap-and-replace solution. We also believe in making everything as frictionless as possible – frictionless for the end-user, frictionless for the developer and frictionless even for the business decision maker. Whatever you offer should be the most sensible thing to do across all parties.
Your perspectives on the future of identity management?
In 2018, Wiley published a book I wrote titled ‘The Digital Identity Crisis’ where I cover all aspects of digital identity and where I think it’s headed. My conclusion is that personal data will continue to expand and create value, but to keep it private we’ll need to have a mechanism that enables each individual to be the owner of their digital identity, so each of us controls and knows exactly how her or his data is being used.